How to encrypt connectionstring in app.config
By Tan Lee Published on Sep 17, 2024 1.01K
Since ASP.NET configuration files are plaintext by default, anyone with server access can view sensitive data such as database usernames and passwords. Fortunately, you can use the ASP.NET IIS Registration tool (aspnet_regiis.exe) to encrypt and decrypt connection strings in your configuration files, enhancing their security.
For example:
<?xml version="1.0" encoding="utf-8"?>
<configuration>
<connectionStrings>
<add name="cn" connectionString="Data Source=192.168.1.123;Initial Catalog=mydb;User ID=sa;Password=123;" providerName="System.Data.SqlClient"/>
</connectionStrings>
</configuration>The aspnet_regiis tool provided by the .NET Framework can be used to encrypt sections of the configuration file.
How to encrypt connectionstring in app.config
Open Command Prompt with administrative privileges. You can do this by searching for cmd in the Start menu, then right-clicking on Command Prompt, and selecting "Run as administrator."
Depending on your version of the .NET Framework, you need to navigate to the appropriate directory.
For .NET Framework 2.x
cd %windir%\Microsoft.NET\Framework\v2.0.50727
For .NET Framework 4.x
cd %windir%\Microsoft.NET\Framework\v4.0.30319
Use the aspnet_regiis tool to encrypt the <connectionStrings> section of your configuration file. Run the following command.
aspnet_regiis -pef "connectionStrings" "C:\YourConfigFolder"
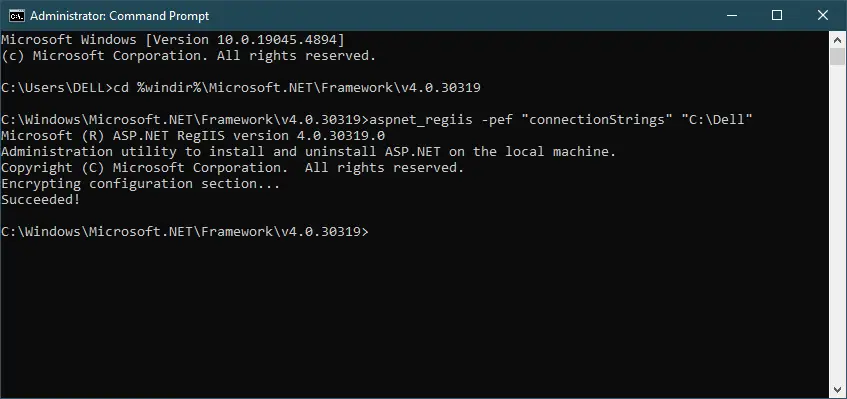
You should replace "C:\YourConfigFolder" with the path to the directory containing your app.config or web.config file.
Open your app.config or web.config file in a text editor to verify that the <connectionStrings> section is now encrypted. It will be encoded and appear in an unreadable format.
<?xml version="1.0" encoding="utf-8"?>
<configuration>
<connectionStrings configProtectionProvider="RsaProtectedConfigurationProvider">
<EncryptedData Type="http://www.w3.org/2001/04/xmlenc#Element"
xmlns="http://www.w3.org/2001/04/xmlenc#">
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#aes256-cbc" />
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<EncryptedKey xmlns="http://www.w3.org/2001/04/xmlenc#">
<EncryptionMethod Algorithm="http://www.w3.org/2001/04/xmlenc#rsa-1_5" />
<KeyInfo xmlns="http://www.w3.org/2000/09/xmldsig#">
<KeyName>Rsa Key</KeyName>
</KeyInfo>
<CipherData>
<CipherValue>LIfmnRveUj/0lreGnibRfEe5b7cJvhHhmNlNSAqsqac7w8pgeZCdbmq2pZFB5Jj4DsEUN282vf7qo+Tg8Vnq4cOKhA9IGRsW4gK7rDTjmrtxR6y92fBPa063CnEXRMkKExRJMD7p4+qZ0zMwQ3B9qRtJs9aYW4at102O8YriSau6we5ibQnLvbqfoHYL4q/GLJqnSQ0NW1cmGK1izw0LfBle3BAfOrui5OrI7rTaEpGXa83FlsTFGBopmXhdwsDRhi76woAdOyPD/1NKsdRJ9W8z8ZfZ/0Dj6riiEEqc/DVm4gX0fUhKCUcmWHMyFYc/8peKrADB06cMGM3rUwJJqQ==</CipherValue>
</CipherData>
</EncryptedKey>
</KeyInfo>
<CipherData>
<CipherValue>BPcEPCPZ9CcEaaDeGeywjGu7opQR1Q9iqOoi+S3MudE6LSPKQtEY97+CZPhcrbrr1WZ25NPBQN5a9+1/myZSjV2lsclmIM7vD2anuwg+0cPNlaa/AhBzanugtsX5aqbHASLNGDUHQfSALBOmOmBF1vMPc9jMMZO4/eg2vzyxQrU94wV02PHlRer4f9FlUe380HhEeW97I23/g0cGFdOAI9mrHutXtOj6mUoyS4/tr2c3WyuQ4kb6jRZBpqUignKGY4QZpEVkBn4YyzxVWgehJyhJxG396r/RenCSXeVxcpQ=</CipherValue>
</CipherData>
</EncryptedData>
</connectionStrings>
</configuration>How to decrypt connectionstring in app.config
If you need to decrypt the configuration section later, you can use the following command.
aspnet_regiis -pdf "connectionStrings" "C:\YourConfigFolder"
Replace "C:\YourConfigFolder" with the actual path.
Using aspnet_regiis is a straightforward way to add an extra layer of security to your sensitive configuration data.
- How to Encrypt and Decrypt files using AES encryption algorithm in C#
- How to Encrypt and Decrypt plain string using RC4 in C#
- How to Encrypt and Decrypt data using RSA in C#
- How to encrypt with MD5 in C#
- How to Encrypt and Decrypt a String in C#
- How to Encrypt and Decrypt ConnectionString in App.config file in C#
- How to Encrypt and Decrypt plain string using ROT13 in C#
- How to Encrypt and Decrypt plain string using Triple DES in C#