How to protect .NET code from reverse engineering
By Tan Lee Published on Jul 12, 2017 7.7K
Several tools, including .NET Reactor by Eziriz, Eziriz itself, and Obfuscation, can be used to add layers of protection to your assemblies.
To play demo, we will create a new project.
Open Visual Studio, then click New Project, then select Visual C# on the left, then Windows and then select Class Library. Name your project "MyMath" and then click OK
Next, Click New Project, then select Visual C# on the left, then Windows and then select Windows Forms Application. Name your project "NetReactor" and then click OK
Design your form as below
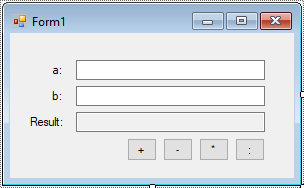
Add a MyMath class to the MyMath library like this:
using System;
using System.Collections.Generic;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
namespace MyMath
{
public class Math
{
public int Add(int a, int b)
{
return a + b;
}
public int Sub(int a, int b)
{
return a - b;
}
public int Mul(int a, int b)
{
return a * b;
}
public double Div(double a, double b)
{
return a / b;
}
}
}Finnaly, Add code to handle your form
using System;
using System.Collections.Generic;
using System.ComponentModel;
using System.Data;
using System.Drawing;
using System.Linq;
using System.Text;
using System.Threading.Tasks;
using System.Windows.Forms;
namespace NetReactor
{
public partial class Form1 : Form
{
public Form1()
{
InitializeComponent();
}
private void btnAdd_Click(object sender, EventArgs e)
{
txtResult.Text = string.Format("a+b={0}", new MyMath.Math().Add(Convert.ToInt32(txta.Text), Convert.ToInt32(txtb.Text)));
}
private void btnSub_Click(object sender, EventArgs e)
{
txtResult.Text = string.Format("a-b={0}", new MyMath.Math().Sub(Convert.ToInt32(txta.Text), Convert.ToInt32(txtb.Text)));
}
private void btnMul_Click(object sender, EventArgs e)
{
txtResult.Text = string.Format("a*b={0}", new MyMath.Math().Mul(Convert.ToInt32(txta.Text), Convert.ToInt32(txtb.Text)));
}
private void btnDiv_Click(object sender, EventArgs e)
{
txtResult.Text = string.Format("a:b={0}", new MyMath.Math().Div(Convert.ToDouble(txta.Text), Convert.ToDouble(txtb.Text)));
}
}
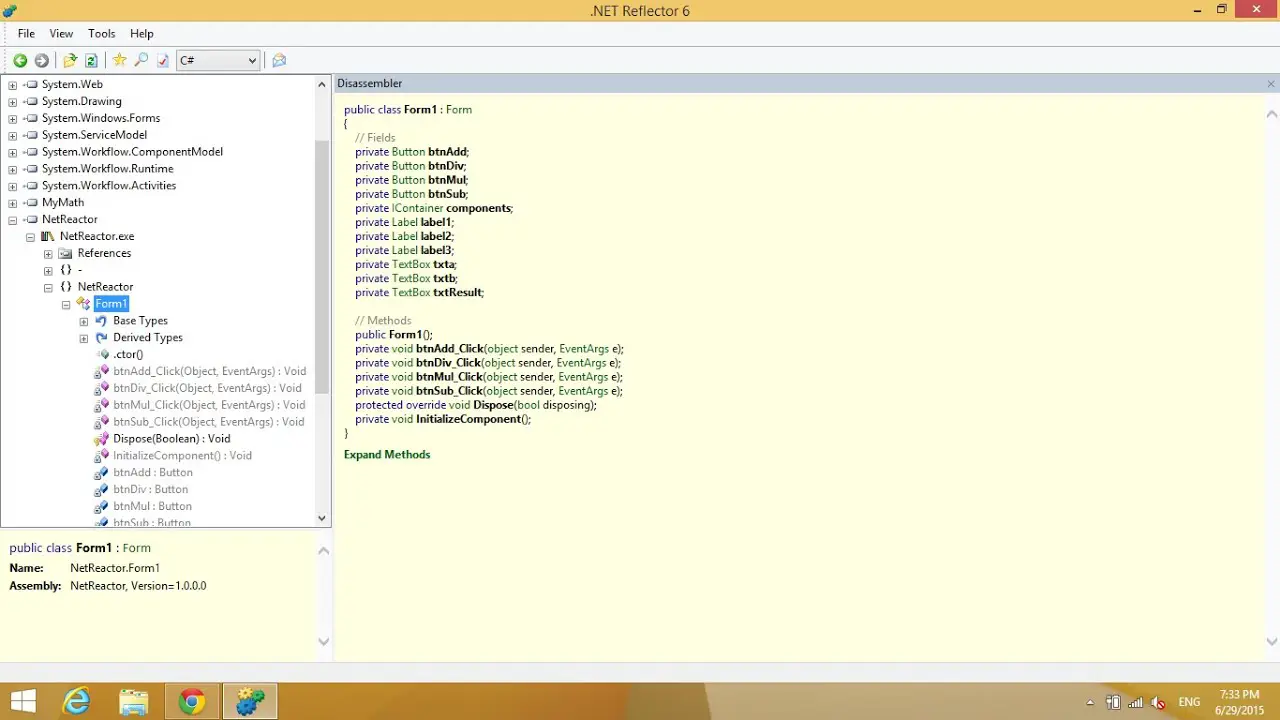
}Download .Net Reactor tool to protect your code.
.NET Reactor is one of the most popular tools for protecting .NET applications from reverse engineering. It combines code obfuscation, encryption, and other forms of protection to make it harder for attackers to decompile and understand your code.
Why you need to protect your intellectual property
When you compile a .NET program, it is not turned into a native executable but rather into Common Intermediate Language (CIL) instructions. CIL sits between source code and machine code, and is interpreted by the .NET framework at runtime instead of being executed directly by the operating system. As a result, the source code of your application or library can be easily extracted or reverse-engineered.
So why is obsfucation not enough?
Obfuscation is the process of making source code harder to understand by replacing meaningful names for classes, methods, properties, and variables with meaningless ones. While it doesn't make reverse engineering impossible, it significantly increases the difficulty of understanding the code.
Obfuscation replaces meaningful names in your code, like "counter," with random, confusing names such as "F6DF3CV89X," making the code harder for humans to understand but not affecting its execution. However, obfuscation doesn't protect the actual logic inside your methods. .NET Reactor goes beyond obfuscation by adding multiple layers of protection, safeguarding your intellectual property and making it much harder for even determined attackers to access or reverse-engineer your source code.
.NET Reactor prevents decompilation by converting your .NET assemblies into a format that cannot be understood by existing decompilation tools. It creates a native code barrier, ensuring that the CIL code is only emitted at runtime or design time, making it impossible for tools to decompile or reverse-engineer .NET Reactor-protected assemblies directly.
VIDEO TUTORIAL
- How to Open and Show a PDF file in C#
- How to Get all Forms and Open Form with Form Name in C#
- How to zoom an image in C#
- How to Print a Picture Box in C#
- How to update UI from another thread in C#
- How to Search DataGridView by using TextBox in C#
- How to read and write to text file in C#
- How to save files using SaveFileDialog in C#